Introduction
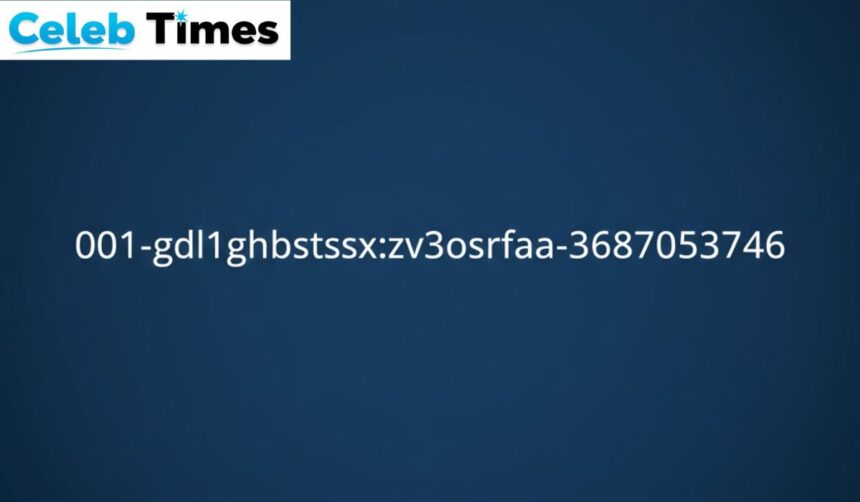
In the rapidly evolving landscape of modern technology and data management, specific identifiers and complex strings often serve as the backbone for sophisticated systems. One such identifier is 001-gdl1ghbstssxzv3os4rfaa-3687053746. While it may appear as a random sequence of alphanumeric characters to the uninitiated, these strings are fundamental to the way digital environments categorize, retrieve, and secure information. Understanding the structure and the underlying logic of such identifiers is crucial for professionals working within specialized technical frameworks, as they often dictate the flow of operations and the integrity of data structures.
- Introduction
- Structural Foundations of Digital Identifiers
- Technical Implementation and Integration
- Role in Secure Data Management
- Operational Efficiency and Scalability
- Common Challenges in System Maintenance
- Future Trends in Identification Logic
- Best Practices for Developers and Architects
- Comparison of Identifier Types
- FAQs
- Conclusion
This article aims to provide an exhaustive exploration of the concepts surrounding this specific topic. We will delve into the technical architecture, the various environments where such identifiers are prevalent, and the best practices for managing them. By breaking down the complexities into digestible segments, we can better appreciate the precision required in modern digital cataloging. Whether you are a developer, a system architect, or a curious enthusiast, this deep dive into 001-gdl1ghbstssxzv3os4rfaa-3687053746 will offer valuable insights into the mechanics of contemporary information systems.
Structural Foundations of Digital Identifiers
The architecture of a digital string is rarely accidental. Most are generated using specific algorithms designed to ensure uniqueness and prevent collisions within a database. In the context of large scale systems, these identifiers act as primary keys or unique signatures that distinguish one entity from billions of others. The composition often involves a mix of hexadecimal values, timestamps, and randomized salts to ensure that even if two items are created at the exact same microsecond, their resulting identifiers remain distinct.
Furthermore, the length and complexity of these strings are directly proportional to the security and scalability needs of the platform. A longer string allows for a wider range of permutations, which is essential for global platforms that handle massive influxes of data daily. By utilizing a structured format, systems can quickly parse the identifier to determine its origin, the type of data it represents, and its priority level. This structural integrity is what allows for the seamless automation of data processing, ensuring that every piece of information finds its correct place in the digital hierarchy.
Technical Implementation and Integration
Integrating complex identifiers into existing software stacks requires a meticulous approach to ensure compatibility and performance. Developers must consider how these strings will be stored, indexed, and retrieved. For instance, using a standard string format in a relational database might not be the most efficient method for high speed queries. Instead, many engineers opt for optimized data types or specialized indexing strategies that can handle the specific length and character set of the identifier.
Beyond storage, the integration phase involves setting up validation protocols. These protocols check the format of the string against predefined rules to prevent errors or malicious injections. In distributed systems, where 001-gdl1ghbstssxzv3os4rfaa-3687053746 might be passed between various microservices, maintaining the consistency of the string is paramount. Any slight modification or truncation during transit could lead to a failure in data synchronization, resulting in “orphaned” records that are inaccessible to the user. Therefore, robust error handling and logging are essential components of a successful implementation.
Role in Secure Data Management
Security is a primary driver behind the adoption of long, complex identifiers. In an era where data breaches are increasingly common, relying on simple, sequential ID numbers is a significant vulnerability. Complex strings are much harder for unauthorized parties to guess or predict. This “security through obscurity” is layered with actual encryption methods to create a formidable defense against data scraping and unauthorized access.
Moreover, these identifiers play a vital role in audit trails and compliance. Because they are unique and immutable, they provide a reliable way to track the lifecycle of a data point. From the moment of creation through every modification and eventually to deletion, the identifier remains a constant reference point. This level of traceability is often a legal requirement in industries like finance and healthcare, where accountability is non-negotiable. By leveraging such sophisticated strings, organizations can ensure that their data management practices meet the highest standards of integrity and security.
Operational Efficiency and Scalability
One might assume that handling such lengthy identifiers would slow down a system, but the opposite is often true when implemented correctly. Modern database engines are built to handle high cardinality data with ease. In fact, using a globally unique identifier allows for easier horizontal scaling. When a database is sharded across multiple servers, a unique string ensures that there are no overlaps between different nodes, eliminating the need for a centralized “ID generator” which can become a bottleneck.
This decentralization is a key factor in achieving high availability. As the system grows, more nodes can be added without the risk of duplicating identifiers. This makes the entire ecosystem more resilient and capable of handling traffic spikes without a hitch. For large enterprises, the ability to scale seamlessly is a competitive advantage, and the use of robust identifiers like 001-gdl1ghbstssxzv3os4rfaa-3687053746 is a fundamental part of that strategy. It allows for a “plug and play” approach to infrastructure, where new components can be integrated with minimal reconfiguration.
Common Challenges in System Maintenance
Despite their benefits, managing complex digital identifiers is not without its hurdles. One of the most frequent issues is “human error” during manual troubleshooting or data entry. Because these strings are not human readable, they are nearly impossible to memorize or transcribe accurately by hand. This necessitates the use of specialized tools for developers and support staff, such as clipboard managers, QR code scanners, or automated lookup interfaces, to interact with the data safely.
Another challenge lies in legacy system compatibility. Older software may have strict limits on character lengths or may not support certain symbols found in modern alphanumeric strings. Upgrading these systems to accommodate new standards can be a costly and time consuming process. Furthermore, as data grows, the storage footprint of these identifiers can become significant. While a few bytes might seem negligible, when multiplied by billions of records, it can lead to increased costs in storage and backup operations. Organizations must balance the need for complexity with the practical constraints of their physical and financial resources.
Future Trends in Identification Logic
The world of digital identification is moving toward even more sophisticated and decentralized models. We are seeing a shift away from centralized authorities toward distributed ledger technologies where identifiers are cryptographically secured and self sovereign. In this future, identifiers could potentially contain embedded metadata that describes the permissions and ownership of the data directly within the string itself. This would further reduce the reliance on central databases for authorization checks.
Additionally, artificial intelligence is beginning to play a role in how these strings are managed and analyzed. Machine learning algorithms can detect patterns in identifier usage to predict system failures or identify potential security threats before they manifest. As identifiers become more “intelligent,” they will likely evolve from static markers to dynamic objects that can adapt to the needs of the network. Keeping an eye on these developments is essential for anyone involved in long term system planning and data strategy, as the way we define 001-gdl1ghbstssxzv3os4rfaa-3687053746 today may look very different in a decade.
Best Practices for Developers and Architects
To maximize the utility of complex identifiers, professionals should adhere to a set of industry standard best practices. First and foremost is the principle of immutability: once an identifier is assigned, it should never be changed. Changing a primary key creates a ripple effect across all related tables and services, often leading to data corruption. Instead, if an entity needs to be updated, the metadata associated with the identifier should change, while the string itself remains constant.
Secondly, developers should always use built-in libraries for generating these strings rather than attempting to write custom “randomizer” functions. Standard libraries are vetted for randomness and collision resistance, providing a level of reliability that is hard to replicate. Lastly, it is wise to implement a “masking” layer for the user interface. While the backend handles the full 001-gdl1ghbstssxzv3os4rfaa-3687053746 string, the frontend can display a shortened version or a user-friendly alias to improve the user experience. This keeps the technical complexity tucked away where it belongs, while providing a clean interface for the end user.
Comparison of Identifier Types
| Feature | Numeric ID | Short Alphanumeric | Complex String (001-…) |
| Uniqueness | Low (Risk of overlap) | Moderate | Extremely High |
| Security | Minimal | Low | High (Non-predictable) |
| Scalability | Difficult (Centralized) | Moderate | Easy (Decentralized) |
| Readability | Excellent | Good | Poor (Machine-focused) |
| Storage Cost | Low | Moderate | High |
FAQs
What is the purpose of such a long identifier?
The length ensures that the identifier is globally unique across different systems and servers. This prevents data collisions where two different items might accidentally share the same ID.
Can these identifiers be customized?
Usually, these are generated by a system algorithm to maintain integrity. While some prefixes can be customized for categorization, the bulk of the string is randomized for security.
Is 001-gdl1ghbstssxzv3os4rfaa-3687053746 sensitive information?
In many cases, the identifier itself is not sensitive, but it acts as a key to sensitive data. Proper access controls should always be in place to ensure only authorized users can use the key to see the underlying info.
How do I handle errors if a string is corrupted?
Validation checks should be performed at the point of entry and during transit. If a string does not match the expected format or checksum, the system should reject it and trigger an error log.
Conclusion
The intricacies of 001-gdl1ghbstssxzv3os4rfaa-3687053746 represent a microcosm of the challenges and triumphs of modern data science. While these strings may seem daunting at first glance, they are the silent workhorses of the digital age, providing the structure, security, and scalability required for global connectivity. By understanding their foundations, implementation strategies, and the security benefits they offer, we can build more resilient systems that stand the test of time.
As we look toward a future defined by even greater volumes of data and more complex networks, the importance of robust identification logic will only grow. Staying informed about best practices and emerging trends ensures that we can navigate this landscape with confidence. Ultimately, these identifiers are more than just text; they are the links that hold our digital world together, ensuring that every byte of information is exactly where it needs to be.